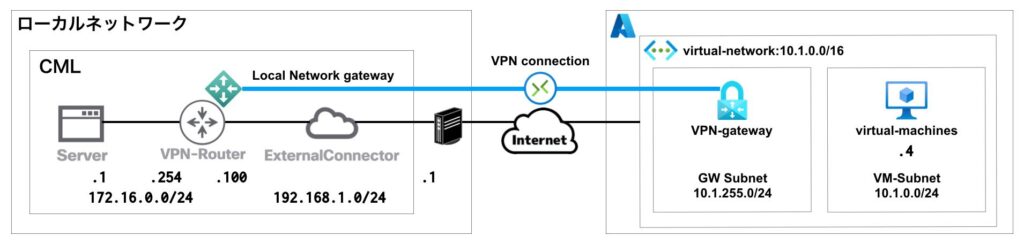
ネットワーク構成
前回までと同様のAzure環境を、AzureCLIを利用して構築します。
下記のネットワーク構成で、CML上のLAN(172.16.0.0/24)とAzure上のサブネット(10.1.0.0/24)が直接通信できるようにします。
※Server(172.16.0.1)からVM(10.1.0.4)にPingによる疎通確認ができるようにしていきます。
AzureCLIのインストール
Windowsの場合
下記より最新バージョンのMSIをダウンロードします。
Windows での Azure CLI のインストール
ダウンロードしたMSIファイルをダブルクリックし、インストールを開始します。
ライセンス条項への同意にチェックを入れ、「Install」をクリックします。
「Completed 〜〜〜〜」と表示されれば、インストールは完了です。
コマンドプロンプロを起動し、下記コマンドを実行し、AzureCLIがインストールされていることを確認します。
az --versionC:¥Users>az --version
azure-cli 2.31.0
core 2.31.0
telemetry 1.0.6
Python location 'C:¥Program Files (x86)¥Microsoft SDKs¥Azure¥CLI2¥python.exe'
Extensions directory 'C:¥Users¥.azure¥cliextensions'
Python (Windows) 3.8.9 (tags/v3.8.9:a743f81, Apr 6 2021, 13:22:56) [MSC v.1928 32 bit (Intel)]
Legal docs and information: aka.ms/AzureCliLegal
Your CLI is up-to-date.
Please let us know how we are doing: https://aka.ms/azureclihats
and let us know if you're interested in trying out our newest features: https://aka.ms/CLIUXstudyMacの場合
ターミナルを起動し、下記コマンドを実行します。
brew update && brew install azure-cli下記コマンドを実行し、AzureCLIがインストールされていることを確認します。
az --versionTerminal[Azure]: az --version
azure-cli 2.31.0
core 2.31.0
telemetry 1.0.6
Python location '/usr/local/Cellar/azure-cli/2.31.0/libexec/bin/python'
Extensions directory '/Users/xxxxxx/.azure/cliextensions'
Python (Darwin) 3.10.1 (main, Dec 6 2021, 23:19:43) [Clang 12.0.0 (clang-1200.0.32.29)]
Legal docs and information: aka.ms/AzureCliLegal
Your CLI is up-to-date.
Please let us know how we are doing: https://aka.ms/azureclihats
and let us know if you're interested in trying out our newest features: https://aka.ms/CLIUXstudyAzureへのログイン
下記のコマンドを実行します。
az loginデフォルトのブラウザが開くので、Microsoftアカウントとパスワードでログインします。ログインが成功すると、Azureのアカウント情報が表示されます。
Terminal[Azure]: az login
The default web browser has been opened at https://login.microsoftonline.com/organizations/oauth2/v2.0/authorize. Please continue the login in the web browser. If no web browser is available or if the web browser fails to open, use device code flow with `az login --use-device-code`.
[
{
"cloudName": "AzureCloud",
"homeTenantId": "********-****-****-****-************",
"id": "********-****-****-****-************",
"isDefault": true,
"managedByTenants": [],
"name": "Azure subscription 1",
"state": "Enabled",
"tenantId": "********-****-****-****-************",
"user": {
"name": "**********@*******.***",
"type": "user"
}
}
]Azureの基本設定
リソースグループの作成
下記コマンドを実行し、リソースグループを作成します。
az group create \
--name rg-azure-vpn-test-002 \
--location japaneastTerminal[Azure]: az group create \
--name rg-azure-vpn-test-002 \
--location japaneast
{
"id": "/subscriptions/********-****-****-****-************/resourceGroups/rg-azure-vpn-test-002",
"location": "japaneast",
"managedBy": null,
"name": "rg-azure-vpn-test-002",
"properties": {
"provisioningState": "Succeeded"
},
"tags": null,
"type": "Microsoft.Resources/resourceGroups"
}仮想ネットワーク・サブネットの作成
下記コマンドを実行し、仮想ネットワークとサブネットを作成します。
az network vnet create \
--resource-group rg-azure-vpn-test-002 \
--name vnet-azure-vpn-test-002 \
--address-prefixes 10.1.0.0/16 \
--subnet-name snet-azure-vpn-test-002 \
--subnet-prefixes 10.1.0.0/24Terminal[Azure]: az network vnet create \
--name vnet-azure-vpn-test-002 \
--resource-group rg-azure-vpn-test-002 \
--address-prefixes 10.1.0.0/16 \
--subnet-name snet-azure-vpn-test-002 \
--subnet-prefixes 10.1.0.0/24
{
"newVNet": {
"addressSpace": {
"addressPrefixes": [
"10.1.0.0/16"
]
},
"bgpCommunities": null,
"ddosProtectionPlan": null,
"dhcpOptions": {
"dnsServers": []
},
"enableDdosProtection": false,
"enableVmProtection": null,
"encryption": null,
"etag": "W/\"********-****-****-****-************\"",
"extendedLocation": null,
"flowTimeoutInMinutes": null,
"id": "/subscriptions/********-****-****-****-************/resourceGroups/rg-azure-vpn-test-002/providers/Microsoft.Network/virtualNetworks/vnet-azure-vpn-test-002",
"ipAllocations": null,
"location": "japaneast",
"name": "vnet-azure-vpn-test-002",
"provisioningState": "Succeeded",
"resourceGroup": "rg-azure-vpn-test-002",
"resourceGuid": "********-****-****-****-************",
"subnets": [
{
"addressPrefix": "10.1.0.0/24",
"addressPrefixes": null,
"applicationGatewayIpConfigurations": null,
"delegations": [],
"etag": "W/\"********-****-****-****-************\"",
"id": "/subscriptions/********-****-****-****-************/resourceGroups/rg-azure-vpn-test-002/providers/Microsoft.Network/virtualNetworks/vnet-azure-vpn-test-002/subnets/snet-azure-vpn-test-002",
"ipAllocations": null,
"ipConfigurationProfiles": null,
"ipConfigurations": null,
"name": "snet-azure-vpn-test-002",
"natGateway": null,
"networkSecurityGroup": null,
"privateEndpointNetworkPolicies": "Enabled",
"privateEndpoints": null,
"privateLinkServiceNetworkPolicies": "Enabled",
"provisioningState": "Succeeded",
"purpose": null,
"resourceGroup": "rg-azure-vpn-test-002",
"resourceNavigationLinks": null,
"routeTable": null,
"serviceAssociationLinks": null,
"serviceEndpointPolicies": null,
"serviceEndpoints": null,
"type": "Microsoft.Network/virtualNetworks/subnets"
}
],
"tags": {},
"type": "Microsoft.Network/virtualNetworks",
"virtualNetworkPeerings": []
}
}ゲートウェイサブネットの作成
下記コマンドを実行し、ゲートウェイサブネットを作成します。
az network vnet subnet create \
--resource-group rg-azure-vpn-test-002 \
--vnet-name vnet-azure-vpn-test-002 \
--name GatewaySubnet \
--address-prefix 10.1.255.0/24Terminal[Azure]: az network vnet subnet create \
--resource-group rg-azure-vpn-test-002 \
--vnet-name vnet-azure-vpn-test-002 \
--name GatewaySubnet \
--address-prefix 10.1.255.0/24
{
"addressPrefix": "10.1.255.0/24",
"addressPrefixes": null,
"applicationGatewayIpConfigurations": null,
"delegations": [],
"etag": "W/\"********-****-****-****-************\"",
"id": "/subscriptions/********-****-****-****-************/resourceGroups/rg-azure-vpn-test-002/providers/Microsoft.Network/virtualNetworks/vnet-azure-vpn-test-002/subnets/GatewaySubnet",
"ipAllocations": null,
"ipConfigurationProfiles": null,
"ipConfigurations": null,
"name": "GatewaySubnet",
"natGateway": null,
"networkSecurityGroup": null,
"privateEndpointNetworkPolicies": "Enabled",
"privateEndpoints": null,
"privateLinkServiceNetworkPolicies": "Enabled",
"provisioningState": "Succeeded",
"purpose": null,
"resourceGroup": "rg-azure-vpn-test-002",
"resourceNavigationLinks": null,
"routeTable": null,
"serviceAssociationLinks": null,
"serviceEndpointPolicies": null,
"serviceEndpoints": null,
"type": "Microsoft.Network/virtualNetworks/subnets"
}AzureのVirtualMachines構築
VirtualMachinesの作成
下記コマンドを実行し、VirtualMachinesを作成します。
az vm create \
--resource-group rg-azure-vpn-test-002 \
--name vmazurevpntest002 \
--image canonical:0001-com-ubuntu-server-focal:20_04-lts-gen2:latest \
--size Standard_B1s \
--public-ip-sku Standard \
--admin-username azureuser \
--nic-delete-option Delete \
--os-disk-delete-option Delete \
--generate-ssh-keysTerminal[Azure]: az vm create \
--resource-group rg-azure-vpn-test-002 \
--name vmazurevpntest002 \
--image canonical:0001-com-ubuntu-server-focal:20_04-lts-gen2:latest \
--size Standard_B1s \
--public-ip-sku Standard \
--admin-username azureuser \
--nic-delete-option Delete \
--os-disk-delete-option Delete \
--generate-ssh-keys
{
"fqdns": "",
"id": "/subscriptions/********-****-****-****-************/resourceGroups/rg-azure-vpn-test-002/providers/Microsoft.Compute/virtualMachines/vmazurevpntest002",
"location": "japaneast",
"macAddress": "00-0D-3A-50-39-0A",
"powerState": "VM running",
"privateIpAddress": "10.1.0.4",
"publicIpAddress": "***.***.***.***",
"resourceGroup": "rg-azure-vpn-test-002",
"zones": ""
}VirtualMachinesへの接続確認
上記コマンドでVirtualMachinesを作成すると、SSH接続に必要な下記情報は “~/.ssh”ディレクトリに格納されるため、下記のコマンドでSSH接続が可能です。
ssh azureuser@***.***.***.*** ※パブリックIPアドレスTerminal[Azure]: ssh azureuser@***.***.***.***
〜〜〜 中略 〜〜〜
Are you sure you want to continue connecting (yes/no)? yes
〜〜〜 中略 〜〜〜
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
azureuser@vmazurevpntest002:~$AzureのVPN構築
パブリックIPアドレスの作成
下記コマンドを実行し、仮想ネットワークゲートウェイ用のパブリックIPアドレスを作成します。
az network public-ip create \
--resource-group rg-azure-vpn-test-002 \
--name pip-azure-vpn-test-002 \
--allocation-method DynamicTerminal[Azure]: az network public-ip create \
--resource-group rg-azure-vpn-test-002 \
--name pip-azure-vpn-test-002 \
--allocation-method Dynamic
{
"publicIp": {
"ddosSettings": null,
"deleteOption": null,
"dnsSettings": null,
"etag": "W/\"********-****-****-****-************\"",
"extendedLocation": null,
"id": "/subscriptions/********-****-****-****-************/resourceGroups/rg-azure-vpn-test-002/providers/Microsoft.Network/publicIPAddresses/pip-azure-vpn-test-002",
"idleTimeoutInMinutes": 4,
"ipAddress": null,
"ipConfiguration": null,
"ipTags": [],
"linkedPublicIpAddress": null,
"location": "japaneast",
"migrationPhase": null,
"name": "pip-azure-vpn-test-002",
"natGateway": null,
"provisioningState": "Succeeded",
"publicIpAddressVersion": "IPv4",
"publicIpAllocationMethod": "Dynamic",
"publicIpPrefix": null,
"resourceGroup": "rg-azure-vpn-test-002",
"resourceGuid": "********-****-****-****-************",
"servicePublicIpAddress": null,
"sku": {
"name": "Basic",
"tier": "Regional"
},
"tags": null,
"type": "Microsoft.Network/publicIPAddresses",
"zones": null
}
}仮想ネットワークゲートウェイの作成
下記コマンドを実行し、仮想ネットワークゲートウェイを作成します。
az network vnet-gateway create \
--resource-group rg-azure-vpn-test-002 \
--name vgw-azure-vpn-test-002 \
--public-ip-address pip-azure-vpn-test-002 \
--vnet vnet-azure-vpn-test-002 \
--gateway-type Vpn \
--sku Basic \
--vpn-type RouteBasedTerminal[Azure]: az network vnet-gateway create \
--resource-group rg-azure-vpn-test-002 \
--name vgw-azure-vpn-test-002 \
--public-ip-address pip-azure-vpn-test-002 \
--vnet vnet-azure-vpn-test-002 \
--gateway-type Vpn \
--sku Basic \
--vpn-type RouteBased
{
"vnetGateway": {
"active": false,
"bgpSettings": {
"asn": 65515,
"bgpPeeringAddress": "10.1.255.254",
"bgpPeeringAddresses": [
{
"customBgpIpAddresses": [],
"defaultBgpIpAddresses": [
"10.1.255.254"
],
"ipconfigurationId": "/subscriptions/********-****-****-****-************/resourceGroups/rg-azure-vpn-test-002/providers/Microsoft.Network/virtualNetworkGateways/vgw-azure-vpn-test-002/ipConfigurations/vnetGatewayConfig0",
"tunnelIpAddresses": [
"***.***.***.***"
]
}
],
"peerWeight": 0
},
"customRoutes": null,
"disableIpSecReplayProtection": false,
"enableBgp": false,
"enableBgpRouteTranslationForNat": false,
"enableDnsForwarding": null,
"enablePrivateIpAddress": false,
"etag": "W/\"********-****-****-****-************\"",
"extendedLocation": null,
"gatewayDefaultSite": null,
"gatewayType": "Vpn",
"id": "/subscriptions/********-****-****-****-************/resourceGroups/rg-azure-vpn-test-002/providers/Microsoft.Network/virtualNetworkGateways/vgw-azure-vpn-test-002",
"inboundDnsForwardingEndpoint": null,
"ipConfigurations": [
{
"etag": "W/\"********-****-****-****-************\"",
"id": "/subscriptions/********-****-****-****-************/resourceGroups/rg-azure-vpn-test-002/providers/Microsoft.Network/virtualNetworkGateways/vgw-azure-vpn-test-002/ipConfigurations/vnetGatewayConfig0",
"name": "vnetGatewayConfig0",
"privateIpAddress": null,
"privateIpAllocationMethod": "Dynamic",
"provisioningState": "Succeeded",
"publicIpAddress": {
"id": "/subscriptions/********-****-****-****-************/resourceGroups/rg-azure-vpn-test-002/providers/Microsoft.Network/publicIPAddresses/pip-azure-vpn-test-002",
"resourceGroup": "rg-azure-vpn-test-002"
},
"resourceGroup": "rg-azure-vpn-test-002",
"subnet": {
"id": "/subscriptions/********-****-****-****-************/resourceGroups/rg-azure-vpn-test-002/providers/Microsoft.Network/virtualNetworks/vnet-azure-vpn-test-002/subnets/GatewaySubnet",
"resourceGroup": "rg-azure-vpn-test-002"
},
"type": "Microsoft.Network/virtualNetworkGateways/ipConfigurations"
}
],
"location": "japaneast",
"name": "vgw-azure-vpn-test-002",
"natRules": [],
"provisioningState": "Succeeded",
"resourceGroup": "rg-azure-vpn-test-002",
"resourceGuid": "********-****-****-****-************",
"sku": {
"capacity": 2,
"name": "Basic",
"tier": "Basic"
},
"tags": null,
"type": "Microsoft.Network/virtualNetworkGateways",
"vNetExtendedLocationResourceId": null,
"vpnClientConfiguration": null,
"vpnGatewayGeneration": "Generation1",
"vpnType": "RouteBased"
}
}ローカルネットワークゲートウェイの作成
自身が利用しているグローバルIPアドレスを確認します。ここではCMANのIPアドレス確認ページで確認しています。
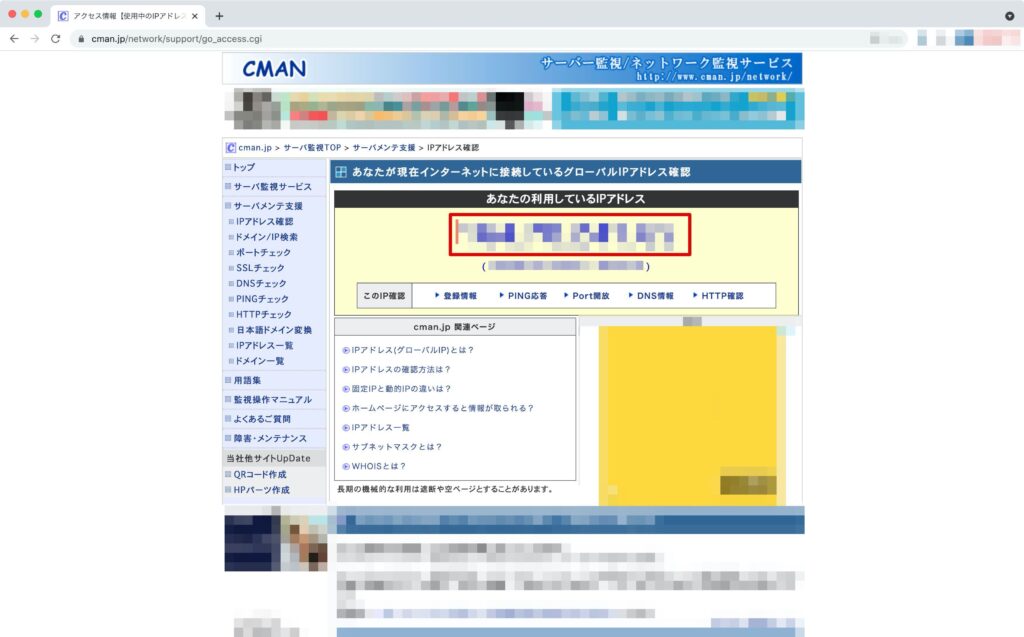
下記コマンドを実行し、ローカルネットワークゲートウェイを作成します。
az network local-gateway create \
--resource-group rg-azure-vpn-test-002 \
--name lgw-azure-vpn-test-002 \
--gateway-ip-address ***.***.***.*** \ ※上記で確認したグローバルIPアドレスを指定
--local-address-prefixes 192.168.1.0/24 172.16.0.0/24Terminal[Azure]: az network local-gateway create \
--resource-group rg-azure-vpn-test-002 \
--name lgw-azure-vpn-test-002 \
--gateway-ip-address ***.***.***.*** \
--local-address-prefixes 192.168.1.0/24 172.16.0.0/24
{
"bgpSettings": null,
"etag": "W/\"********-****-****-****-************\"",
"fqdn": null,
"gatewayIpAddress": "***.***.***.***",
"id": "/subscriptions/********-****-****-****-************/resourceGroups/rg-azure-vpn-test-002/providers/Microsoft.Network/localNetworkGateways/lgw-azure-vpn-test-002",
"localNetworkAddressSpace": {
"addressPrefixes": [
"192.168.1.0/24",
"172.16.0.0/24"
]
},
"location": "japaneast",
"name": "lgw-azure-vpn-test-002",
"provisioningState": "Succeeded",
"resourceGroup": "rg-azure-vpn-test-002",
"resourceGuid": "********-****-****-****-************",
"tags": null,
"type": "Microsoft.Network/localNetworkGateways"
}接続の作成
下記コマンドを実行し、接続を作成します。
az network vpn-connection create \
--resource-group rg-azure-vpn-test-002 \
--name vcn-azure-vpn-test-002 \
--vnet-gateway1 vgw-azure-vpn-test-002 \
--local-gateway2 lgw-azure-vpn-test-002 \
--shared-key ******************** ※任意の文字列を指定Terminal[Azure]: az network vpn-connection create \
--resource-group rg-azure-vpn-test-002 \
--name vcn-azure-vpn-test-002 \
--vnet-gateway1 vgw-azure-vpn-test-002 \
--local-gateway2 lgw-azure-vpn-test-002 \
--shared-key ********************
{
"resource": {
"connectionMode": "Default",
"connectionProtocol": "IKEv2",
"connectionStatus": "Unknown",
"connectionType": "IPsec",
"dpdTimeoutSeconds": 0,
"egressBytesTransferred": 0,
"enableBgp": false,
"ingressBytesTransferred": 0,
"localNetworkGateway2": {
"id": "/subscriptions/********-****-****-****-************/resourceGroups/rg-azure-vpn-test-002/providers/Microsoft.Network/localNetworkGateways/lgw-azure-vpn-test-002",
"resourceGroup": "rg-azure-vpn-test-002"
},
"provisioningState": "Succeeded",
"resourceGuid": "********-****-****-****-************",
"routingWeight": 10,
"sharedKey": "********************",
"trafficSelectorPolicies": [],
"useLocalAzureIpAddress": false,
"virtualNetworkGateway1": {
"id": "/subscriptions/********-****-****-****-************/resourceGroups/rg-azure-vpn-test-002/providers/Microsoft.Network/virtualNetworkGateways/vgw-azure-vpn-test-002",
"resourceGroup": "rg-azure-vpn-test-002"
}
}
}CMLの構築
設定サンプルのダウンロード
設定のサンプルは下記のコマンドで表示できます。
az network vpn-connection show-device-config-script \
--resource-group rg-azure-vpn-test-002 \
--name vcn-azure-vpn-test-002 \
--vendor "Cisco" \
--device-family "IOS (ISR, ASR)" \
--firmware-version "15.x (IKEv2)" \
--output tableTerminal[Azure]: az network vpn-connection show-device-config-script \
--resource-group rg-azure-vpn-test-002 \
--name vcn-azure-vpn-test-002 \
--vendor "Cisco" \
--device-family "IOS (ISR, ASR)" \
--firmware-version "15.x (IKEv2)" \
--output table
This command is in preview and under development. Reference and support levels: https://aka.ms/CLI_refstatus
Result
------------------------------------------------------------------------------------------
! Microsoft Corporation
! ------------------------------------------------------------------------------
! Sample VPN tunnel configuration template for Cisco IOS-based devices
!
! ##############################################################################
! !!! Search for "REPLACE" to find the values that require special
! !!! considerations
! !!!
! !!! (1) ACL/access-list rule numbers
! !!! (2) Tunnel interface number
! !!! (3) Tunnel interface IP address
! !!! (4) BGP routes to advertise (if BGP is enabled)
! !!! (5) BGP peer IP address on the device - loopback interface number
! ##############################################################################
!
! [0] Device infomration
!
! > Device vendor: Cisco
! > Device family: IOS-based (ASR, ISR)
! > Firmware version: IOS 15.1 or beyond
! > Test platform: Cisco ISR 2911, version 15.2
!
! [1] Network parameters
!
! > Connection name: vcn-azure-vpn-test-002
! > VPN Gateway name: ********-****-****-****-************
! > Public IP addresses:
! + Public IP 1: ***.***.***.***
! > Virtual network address space:
! + CIDR:10.1.0.0/16, prefix:10.1.0.0, netmask:255.255.0.0, wildcard:0.0.255.255
! > Local network gateway: lgw-azure-vpn-test-002
! > On-premises VPN IP: ***.***.***.***
! > On-premises address prefixes:
! + CIDR:192.168.1.0/24, prefix:192.168.1.0, netmask:255.255.255.0, wildcard:0.0.0.255
! + CIDR:172.16.0.0/24, prefix:172.16.0.0, netmask:255.255.255.0, wildcard:0.0.0.255
!
! [2] IPsec/IKE parameters
!
! > IKE version: IKEv2
! + Encryption algorithm: aes-cbc-256
! + Integrityalgorithm: sha1
! + Diffie-Hellman group: 2
! + SA lifetime (seconds): 3600
! + Pre-shared key: bkXJkEHKw6L36oUGQmaC
! + UsePolicyBasedTS: False
!
! > IPsec
! + Encryption algorithm: esp-gcm 256
! + Integrity algorithm:
! + PFS Group: none
! + SA lifetime (seconds): 3600
! + SA lifetime (KB): 102400000
!
! [3] BGP parameters - Azure VPN gateway
!
! > Azure virtual network
! + Enable BGP: False
! + Azure BGP ASN: VNG_ASN
! > On-premises network / LNG
! + On premises BGP ASN: LNG_ASN
! + On premises BGP IP: LNG_BGPIP
!
! ==============================================================================
! Cisco IOS 15.x+ IKEv2, route-based (any-to-any)
! ==============================================================================
!
! ACL rules
!
! Some VPN devices require explicit ACL rules to allow cross-premises traffic:
!
! 1. Allow traffic between on premises address ranges and VNet address ranges
! 2. Allow IKE traffic (UDP:500) between on premises VPN devices and Azure VPN gateway
! 3. Allow IPsec traffic (Proto:ESP) between on premises VPN devices and Azure VPN gateway
! [REPLACE] access-list number: access-list 101
access-list 101 permit ip 192.168.1.0 0.0.0.255 10.1.0.0 0.0.255.255
access-list 101 permit ip 172.16.0.0 0.0.0.255 10.1.0.0 0.0.255.255
access-list 101 permit esp host ***.***.***.*** host ***.***.***.***
access-list 101 permit udp host ***.***.***.*** eq isakmp host ***.***.***.***
access-list 101 permit udp host ***.***.***.*** eq non500-isakmp host ***.***.***.***
! ==============================================================================
! Internet Key Exchange (IKE) configuration
! - IKE Phase 1 / Main mode configuration
! - Encryption/integrity algorithms, Diffie-Hellman group, pre-shared key
crypto ikev2 proposal vcn-azure-vpn-test-002-proposal
encryption aes-cbc-256
integrity sha1
group 2
exit
crypto ikev2 policy vcn-azure-vpn-test-002-policy
proposal vcn-azure-vpn-test-002-proposal
match address local ***.***.***.***
exit
crypto ikev2 keyring vcn-azure-vpn-test-002-keyring
peer ***.***.***.***
address ***.***.***.***
pre-shared-key ********************
exit
exit
crypto ikev2 profile vcn-azure-vpn-test-002-profile
match address local ***.***.***.***
match identity remote address ***.***.***.*** 255.255.255.255
authentication remote pre-share
authentication local pre-share
lifetime 3600
dpd 10 5 on-demand
keyring local vcn-azure-vpn-test-002-keyring
exit
! ------------------------------------------------------------------------------
! IPsec configuration
! - IPsec (or IKE Phase 2 / Quick Mode) configuration
! - Transform Set: IPsec encryption/integrity algorithms, IPsec ESP mode
crypto ipsec transform-set vcn-azure-vpn-test-002-TransformSet esp-gcm 256
mode tunnel
exit
crypto ipsec profile vcn-azure-vpn-test-002-IPsecProfile
set transform-set vcn-azure-vpn-test-002-TransformSet
set ikev2-profile vcn-azure-vpn-test-002-profile
set security-association lifetime seconds 3600
exit
! ------------------------------------------------------------------------------
! Tunnel interface (VTI) configuration
! - Create/configure a tunnel interface
! - Configure an APIPA (169.254.x.x) address that does NOT overlap with any
! other address on this device. This is not visible from the Azure gateway.
! * REPLACE: Tunnel interface numbers and APIPA IP addresses below
! * Default tunnel interface 11 (169.254.0.1) and 12 (169.254.0.2)
int tunnel 11
ip address 169.254.0.1 255.255.255.255
tunnel mode ipsec ipv4
ip tcp adjust-mss 1350
tunnel source ***.***.***.***
tunnel destination ***.***.***.***
tunnel protection ipsec profile vcn-azure-vpn-test-002-IPsecProfile
exit
! ------------------------------------------------------------------------------
! Static routes
! - Adding the static routes to point the VNet prefixes to the IPsec tunnels
! * REPLACE: Tunnel interface number(s), default tunnel 11 and tunnel 12
ip route 10.1.0.0 255.255.0.0 Tunnel 11
! ==============================================================================
! Cleanup script
! ==============================================================================
!
! [WARNING] This section of the script will cleanup the resources: IPsec/IKE,
! [WARNING] interfaces, routes, access-list. Validate the objects in your
! [WARNING] configuration before applying the script below.
! [REPLACE] Interfaces: Loopback 11, Tunnel 11, Tunnel 12; access-list 101
!
!!
!! no ip route 10.1.0.0 255.255.0.0 Tunnel 11
!!
!!
!! no int tunnel 11
!!
!! no crypto ipsec profile vcn-azure-vpn-test-002-IPsecProfile
!! no crypto ipsec transform-set vcn-azure-vpn-test-002-TransformSet
!!
!! no crypto ikev2 profile vcn-azure-vpn-test-002-profile
!! no crypto ikev2 keyring vcn-azure-vpn-test-002-keyring
!! no crypto ikev2 policy vcn-azure-vpn-test-002-policy
!! no crypto ikev2 proposal vcn-azure-vpn-test-002-proposal
!!
!! no access-list 101 permit ip 192.168.1.0 0.0.0.255 10.1.0.0 0.0.255.255
!! no access-list 101 permit ip 172.16.0.0 0.0.0.255 10.1.0.0 0.0.255.255
!! no access-list 101 permit esp host ***.***.***.*** host ***.***.***.***
!! no access-list 101 permit udp host ***.***.***.*** eq isakmp host ***.***.***.***
!! no access-list 101 permit udp host ***.***.***.*** eq non500-isakmp host ***.***.***.***CML構築
CMLの構築に関しては、以下を参照してください。
Azureサイト間VPNの構築(4.CMLの構築)
以上で、Azureサイト間VPNの構築(5.Azure CLI によるVPN接続の作成)の説明は完了です!









